Tutorial over G-Cloud infrastructure
Repo :: github-link
Hello people, in this lab, we will create a terraform configuration with a module to automate the deployment of Google Cloud infrastructure. Specifically, you deploy one auto-mode network with a firewall rule and two VM instances, as shown in this diagram:

Tasks --
Create a configuration for an auto-mode network.
Create a configuration for a firewall rule.
Create a module for VM instances.
Create and deploy a configuration.
Verify the deployment of a configuration.
Task 1. Set up Terraform and Cloud Shell
Terraform is now integrated into Cloud Shell. Verify which version is installed.
In the Cloud Console, click Activate Cloud Shell ().
If prompted, click Continue.
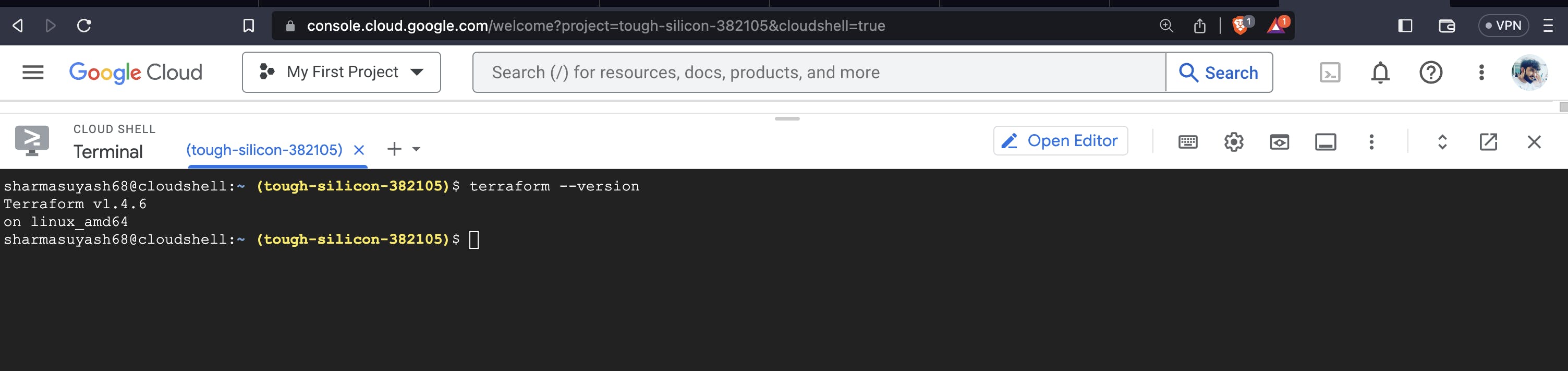
To confirm that Terraform is installed, run the following command:
terraform --version
The output should look like this:
- To create a directory for your Terraform configuration, run the following command:
mkdir tfinfra
- Create the file into tfinfra directory named as
provider.tf:
provider "google" {}
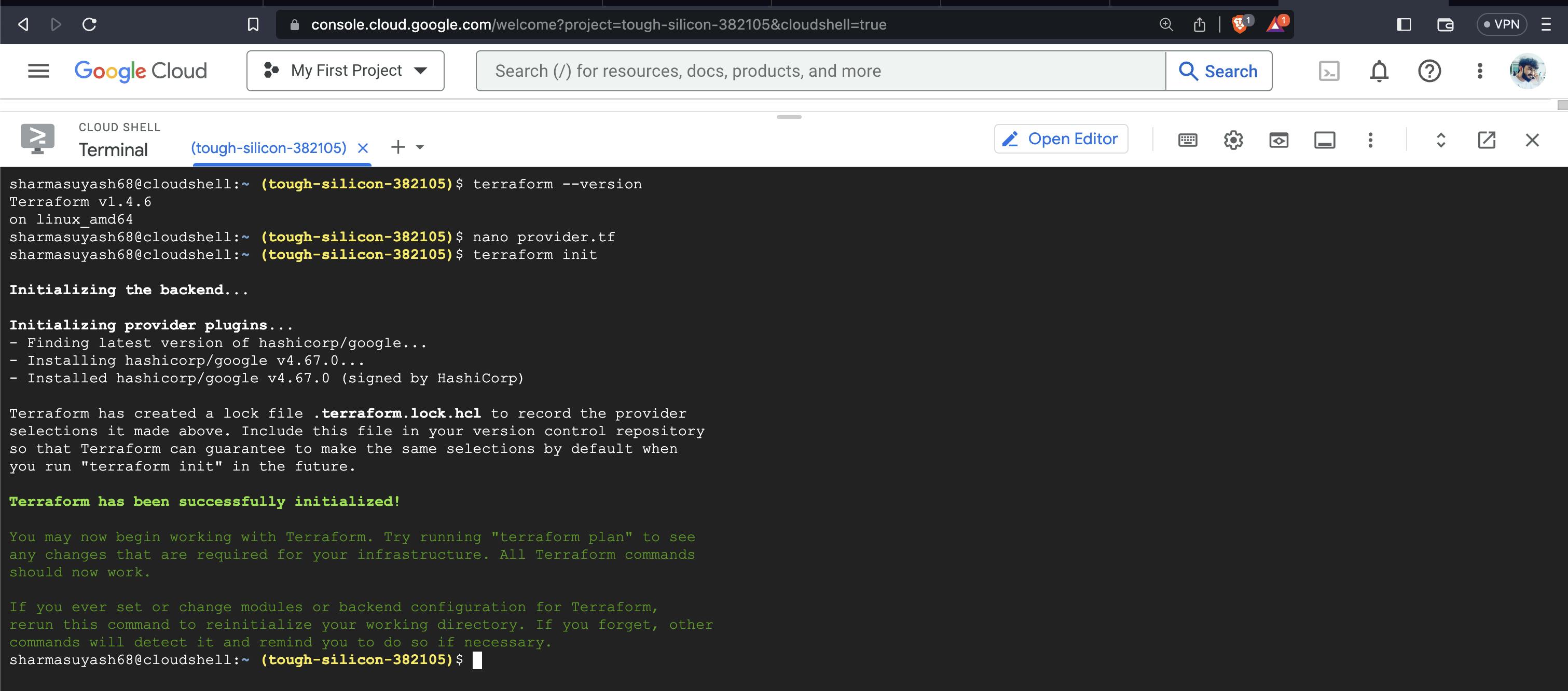
To initialize Terraform, run the following command:
cd tfinfra terraform initThe output should look like this:
Task 2. Create mynetwork and its resources
Create a new configuration, and define mynetwork.tf, which includes,
1 - firewall rule to allow HTTP, SSH, RDP, and ICMP traffic on mynetwork.
2 - the VM instances by creating a VM instance module
3 - Create a variables.tf file and define variables according to below tf configuration,
#variables.tf
variable "instance_name" {}
variable "instance_zone" {}
variable "instance_type" {
default = "e2-micro"
}
variable "instance_network" {}
#mynetwork.tf
# Create the mynetwork network
resource "google_compute_network" "mynetwork" {
name = "mynetwork"
# RESOURCE properties go here
auto_create_subnetworks = "true"
}
# Add a firewall rule to allow HTTP, SSH, RDP and ICMP traffic on mynetwork
resource "google_compute_firewall" "mynetwork-allow-http-ssh-rdp-icmp" {
name = "mynetwork-allow-http-ssh-rdp-icmp"
# RESOURCE properties go here
network = google_compute_network.mynetwork.self_link
allow {
protocol = "tcp"
ports = ["22", "80", "3389"]
}
allow {
protocol = "icmp"
}
source_ranges = ["0.0.0.0/0"]
}
resource "google_compute_instance" "vm_instance" {
name = "mynet-us-vm"
zone = "us-central1-a"
machine_type = var.instance_type
boot_disk {
initialize_params {
image = "debian-cloud/debian-11"
}
}
network_interface {
network = google_compute_network.mynetwork.self_link
access_config {
# Allocate a one-to-one NAT IP to the instance
}
}
}
resource "google_compute_instance" "vm_instance1" {
name = "mynet-eu-vm"
zone = "europe-west1-d"
machine_type = var.instance_type
boot_disk {
initialize_params {
image = "debian-cloud/debian-11"
}
}
network_interface {
network = google_compute_network.mynetwork.self_link
access_config {
# Allocate a one-to-one NAT IP to the instance
}
}
}
Task 3. Apply to terraform and trigger
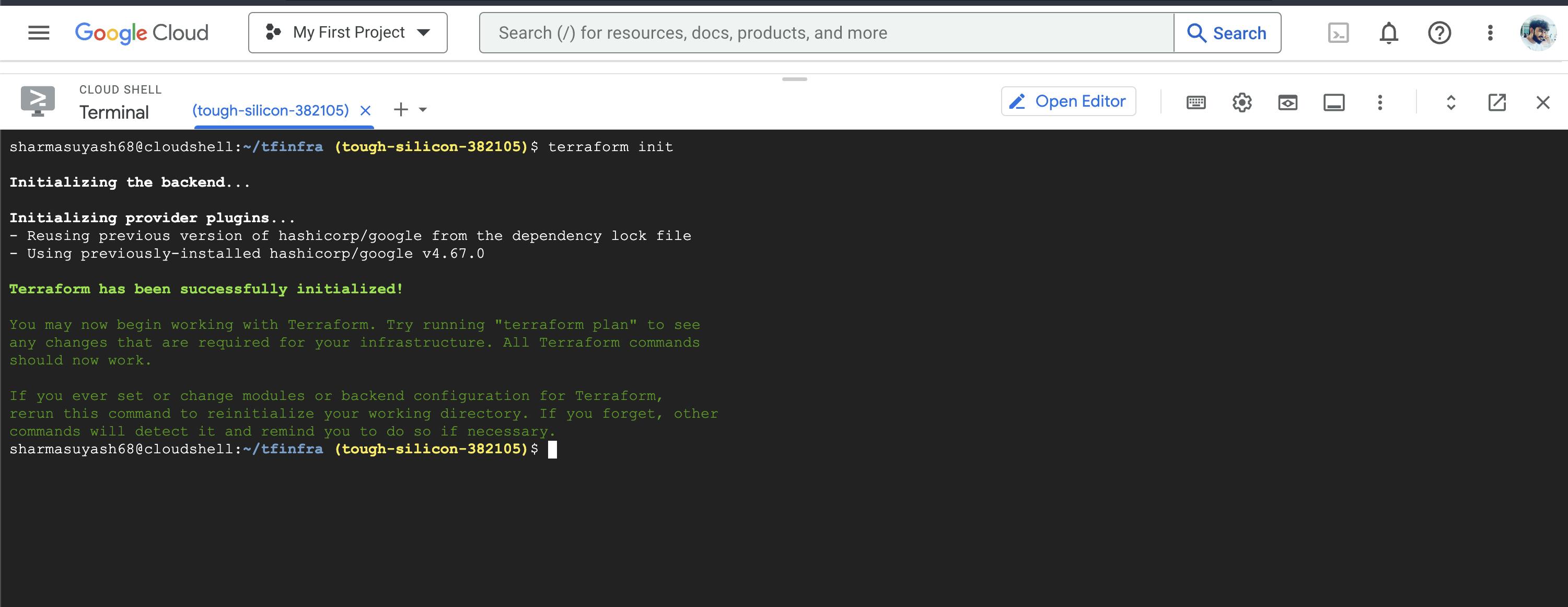
To initialize Terraform, run the following command:
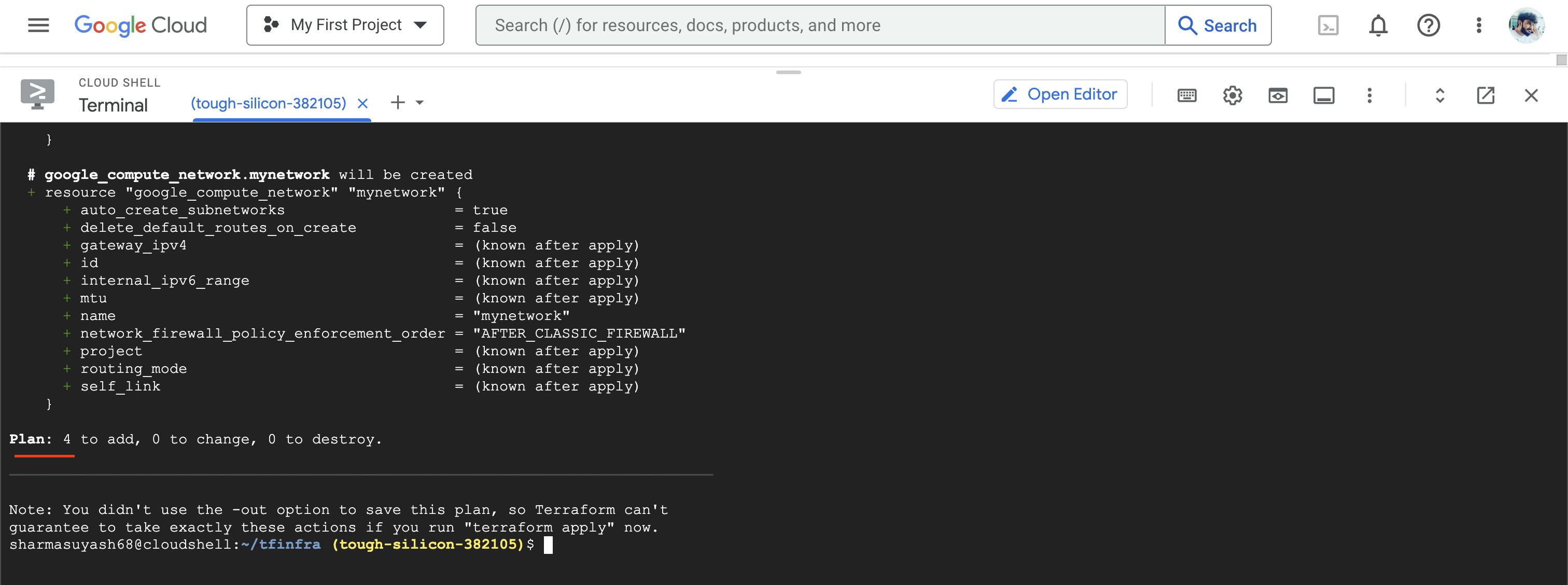
To create an execution plan, run the following command:
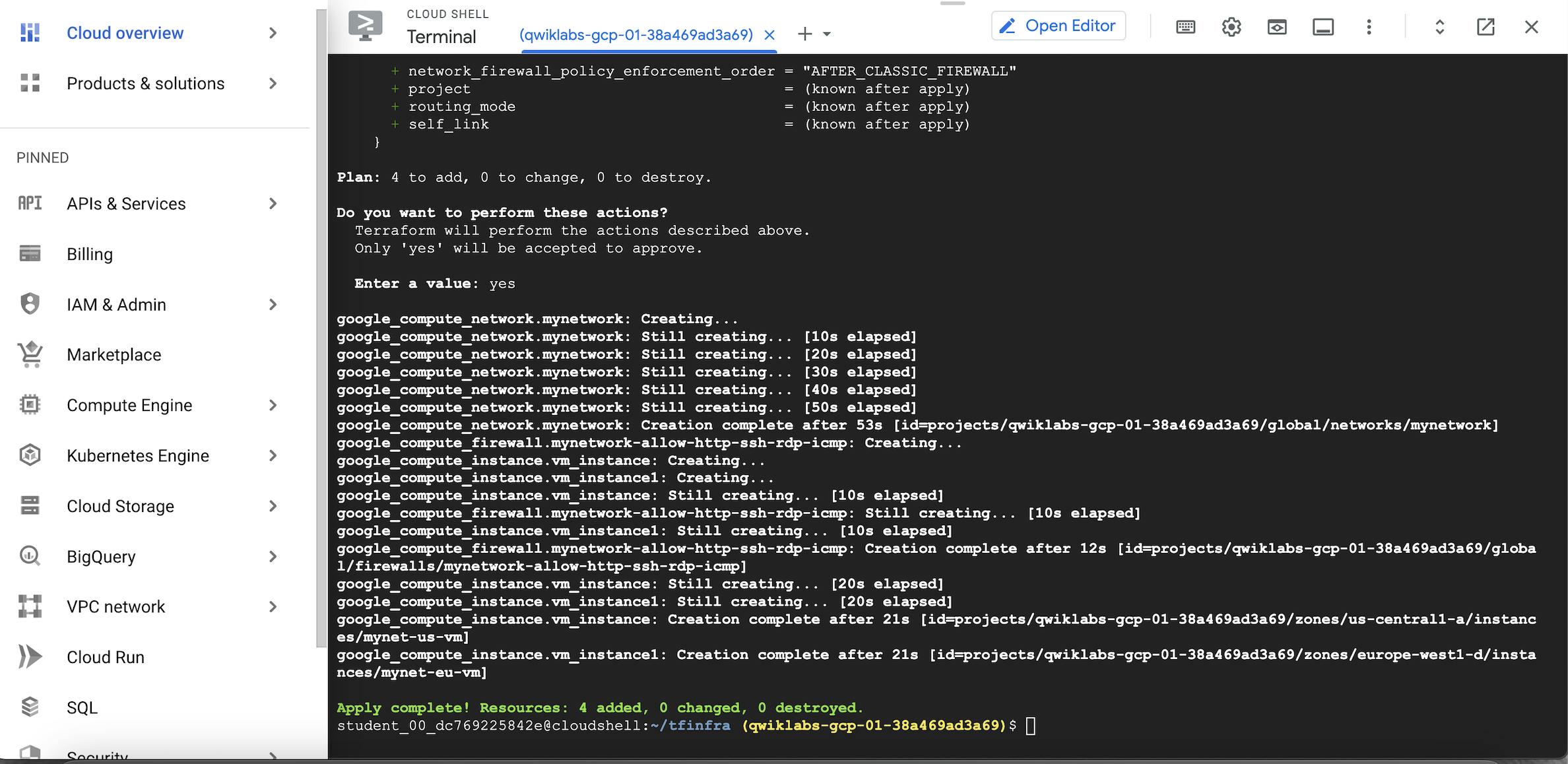
To apply the desired changes, run the following command:
terraform apply
To confirm the planned actions, type:
yes
The output should look like this:
Task 4. Verify your deployment
Verify your network in the Cloud Console
In the Cloud Console, on the Navigation menu (), click VPC network > VPC networks.
View the mynetwork VPC network with a subnetwork in every region.
On the Navigation menu, click VPC network > Firewall.
Sort the firewall rules by Network.
View the mynetwork-allow-http-ssh-rdp-icmp firewall rule for mynetwork.
Verify your VM instances in the Cloud Console
On the Navigation menu (), click Compute Engine > VM instances.
View the mynet-us-vm and mynet-eu-vm instances.
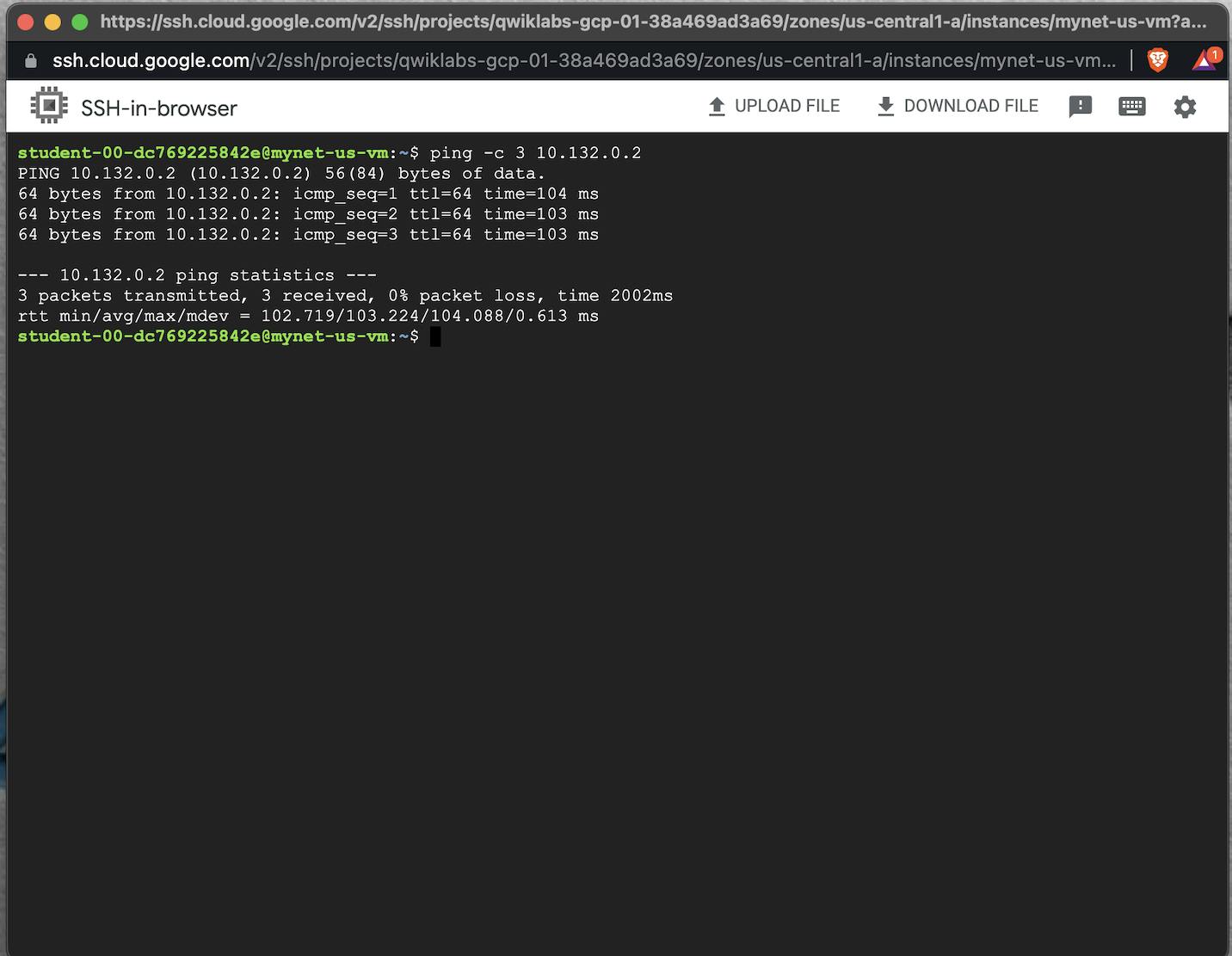
Note the internal IP address for mynet-eu-vm.
For mynet-us-vm, click SSH to launch a terminal and connect.
To test connectivity to mynet-eu-vm's internal IP address, run the following command in the SSH terminal (replacing mynet-eu-vm's internal IP address with the value noted earlier):
ping -c 3 <Enter mynet-eu-vm's internal IP here>
Thank you for looking at this article, please give a thumbsup if it helped you.
